HTB - Planning Writeup
Step-by-step walkthrough for the HackTheBox 'Planning' machine: enumeration, subdomain fuzzing, exploiting Grafana, privilege escalation via Crontab UI, and root access.
HTB - Planning Writeup
HTB - Planning Writeup
Introduction
The “Planning” machine on HackTheBox simulates a real-world pentest. We’ll cover enumeration, exploitation, and privilege escalation, explaining the reasoning behind each step. You start with provided credentials, just like in many internal assessments.
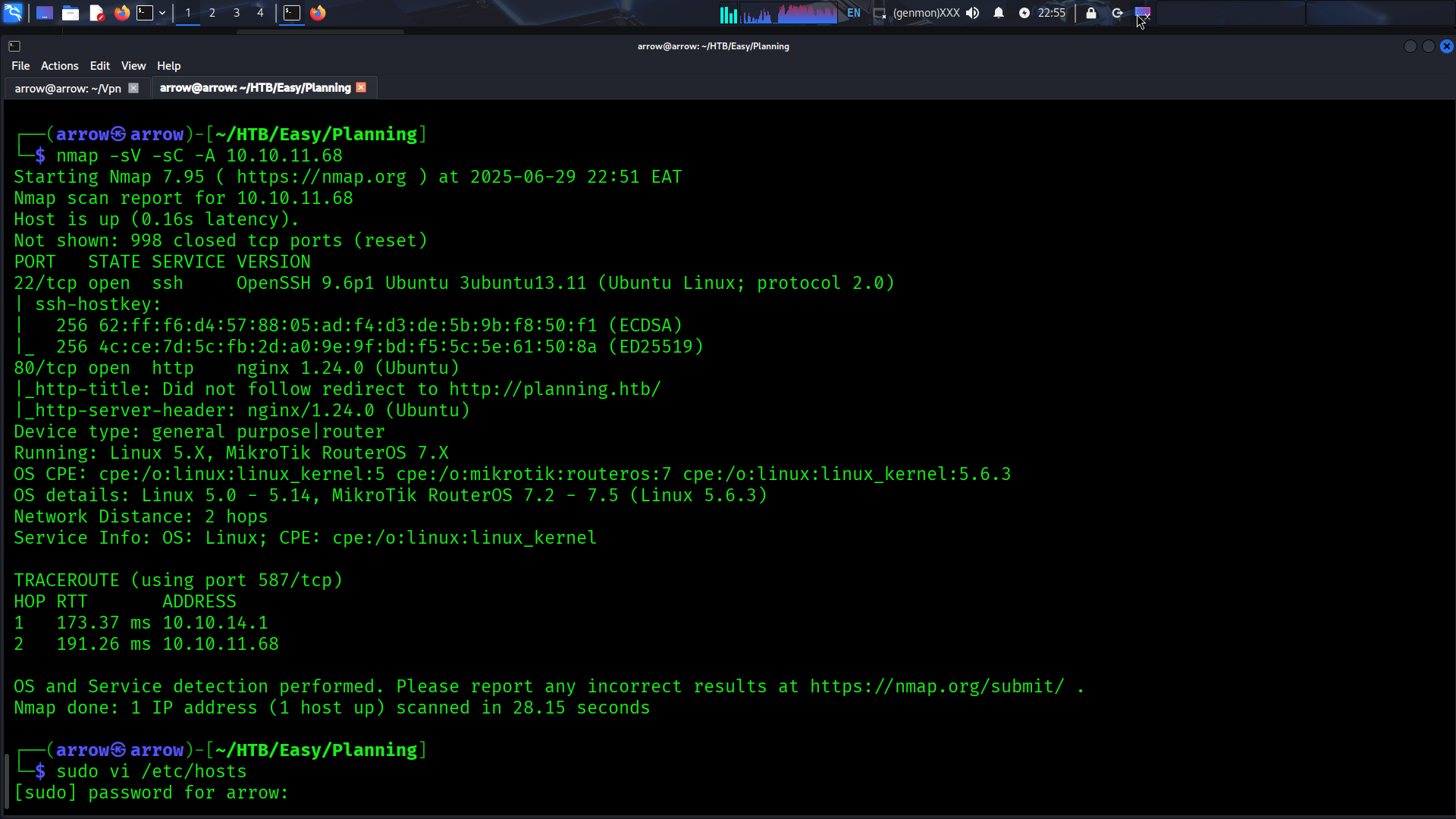
Initial Access & Machine Information
You are given credentials to begin:
1
admin / 0D5oT70Fq13EvB5r
...
This post is licensed under CC BY 4.0 by the author.
💡 Like what you’re reading?
If this write-up added value to your learning or workflow, feel free to support continued content like this.
☕ Support via PayPal